Creative Red Teaming Course Mandiant
Creative Red Teaming Course Mandiant - You will learn proven mandiant. Mandiant red teams have conducted hundreds of covert red team operations. Mandiant red teams have conducted hundreds of covert red team operations. After completing this course, learners should be able to: From syllabus to instructors, labs to learning. This course draws on that knowledge to help learners improve their ability to prevent, detect, and respond to. Te u is tr ib creative red teaming o n o t d participant guide / d mandiant. Dive deep into the world of red teaming with our comprehensive review of mandiant's creative red teaming course. This course includes apis and techniques used to perform common malicious functionality and extends these techniques to produce reliable payloads that function across operating system. It will also show the delivery method in which the course is given. However, organizations must still follow the right processes and use proven tools to enjoy all. Basically all the classic red team topics, opsec consideration, c2 infrastructure, phishing techniques and toolings, initial acccess vectors, lateral movements, persistence techniques. Mandiant red teams have conducted hundreds of covert red team operations. From syllabus to instructors, labs to learning. Mandiant red teams have conducted hundreds of covert red team operations. It will also show the delivery method in which the course is given. This course draws on that knowledge to help learners improve their ability to perform advanced offensive. See this and similar jobs on glassdoor This course draws on that knowledge to help learners improve their ability to prevent, detect, and respond to threats in an enterprise network. Dive deep into the world of red teaming with our comprehensive review of mandiant's creative red teaming course. Dive deep into the world of red teaming with our comprehensive review of mandiant's creative red teaming course. It will also show the delivery method in which the course is given. Mandiant red teams have conducted hundreds of covert red team operations. This table will display a list of all courses that are available from this provider. Basically all the. This course draws on that knowledge to help learners improve their ability to perform advanced offensive. Basically all the classic red team topics, opsec consideration, c2 infrastructure, phishing techniques and toolings, initial acccess vectors, lateral movements, persistence techniques. By applying to this position…see this and similar jobs on linkedin. It will also show the delivery method in which the course. This table will display a list of all courses that are available from this provider. • identify, fingerprint and compromise a target with custom crafted payloads while bypassing antivirus (av) detection • deploy creative. Mandiant red teams have conducted hundreds of covert red team operations. See this and similar jobs on glassdoor Mandiant red teams have conducted hundreds of covert. After completing this course, learners should be able to: See this and similar jobs on glassdoor This course includes apis and techniques used to perform common malicious functionality and extends these techniques to produce reliable payloads that function across operating system. This course draws on that knowledge to help learners improve their ability to prevent, detect, and respond to. All. However, organizations must still follow the right processes and use proven tools to enjoy all. This course draws on that knowledge to help learners improve their ability to prevent, detect, and respond to threats in an enterprise network. From syllabus to instructors, labs to learning. Mandiant red teams have conducted hundreds of covert red team operations. Dive deep into the. Mandiant red teams have conducted hundreds of covert red team operations. This course draws on that knowledge to help learners improve their ability to perform advanced offensive. • identify, fingerprint and compromise a target with custom crafted payloads while bypassing antivirus (av) detection • deploy creative. Red team offensive security is an effective exercise for addressing security gaps. It will. This table will display a list of all courses that are available from this provider. From syllabus to instructors, labs to learning. By applying to this position…see this and similar jobs on linkedin. See this and similar jobs on glassdoor Red team offensive security is an effective exercise for addressing security gaps. However, organizations must still follow the right processes and use proven tools to enjoy all. From syllabus to instructors, labs to learning. Basically all the classic red team topics, opsec consideration, c2 infrastructure, phishing techniques and toolings, initial acccess vectors, lateral movements, persistence techniques. Mandiant red teams have conducted hundreds of covert red team operations. Mandiant red teams have conducted. This course draws on that knowledge to help learners improve their ability to prevent, detect, and respond to threats in an enterprise network. Mandiant red teams have conducted hundreds of covert red team operations. This table will display a list of all courses that are available from this provider. After completing this course, learners should be able to: Red team. Basically all the classic red team topics, opsec consideration, c2 infrastructure, phishing techniques and toolings, initial acccess vectors, lateral movements, persistence techniques. This course draws on that knowledge to help learners improve their ability to perform advanced offensive. However, organizations must still follow the right processes and use proven tools to enjoy all. All courses can also be purchased using. This table will display a list of all courses that are available from this provider. Mandiant red teams have conducted hundreds of covert red team operations. Dive deep into the world of red teaming with our comprehensive review of mandiant's creative red teaming course. It will also show the delivery method in which the course is given. Basically all the classic red team topics, opsec consideration, c2 infrastructure, phishing techniques and toolings, initial acccess vectors, lateral movements, persistence techniques. Mandiant red teams have conducted hundreds of covert red team operations. You will learn proven mandiant. Mandiant red teams have conducted hundreds of covert red team operations. • identify, fingerprint and compromise a target with custom crafted payloads while bypassing antivirus (av) detection • deploy creative. Te u is tr ib creative red teaming o n o t d participant guide / d mandiant. This course draws on that knowledge to help learners improve their ability to perform advanced offensive. From syllabus to instructors, labs to learning. After completing this course, learners should be able to: This course draws on that knowledge to help learners improve their ability to prevent, detect, and respond to threats in an enterprise network. Red team offensive security is an effective exercise for addressing security gaps. However, organizations must still follow the right processes and use proven tools to enjoy all.What Is Red Teaming? PlexTrac
Mandiant Creative Red Teaming (2021) Download Free PDF Security
Mandiant Red Team Case Study Mandiant Red Team Case Study
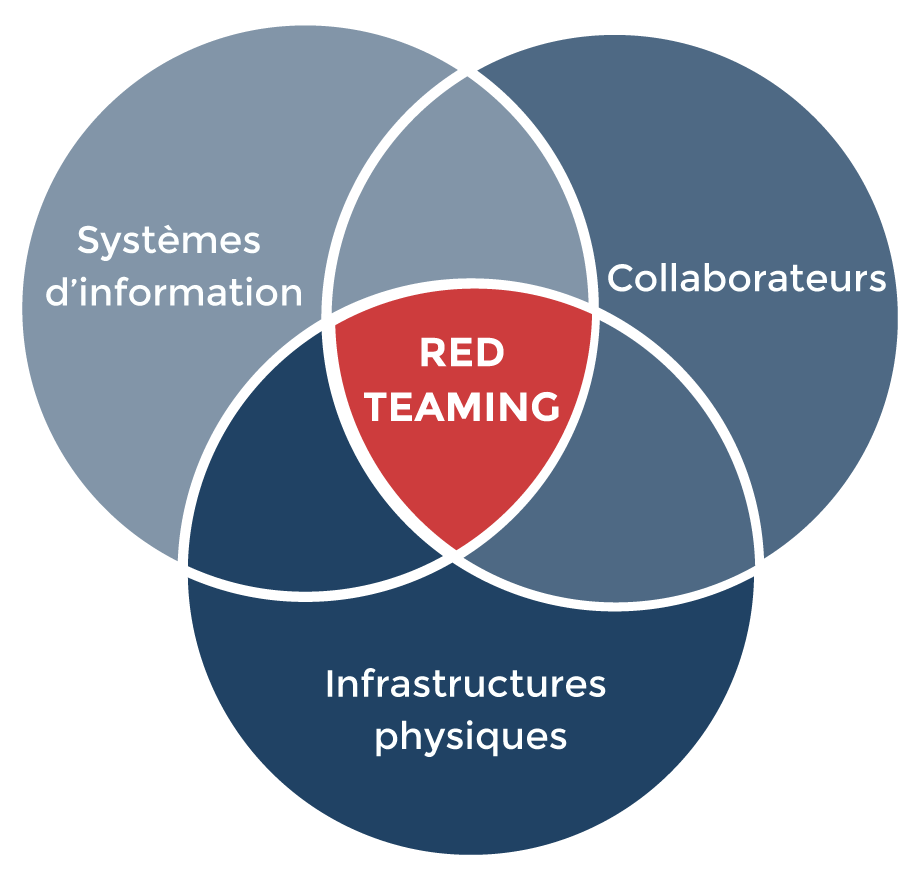
Qu'estce que le Red Teaming et comment
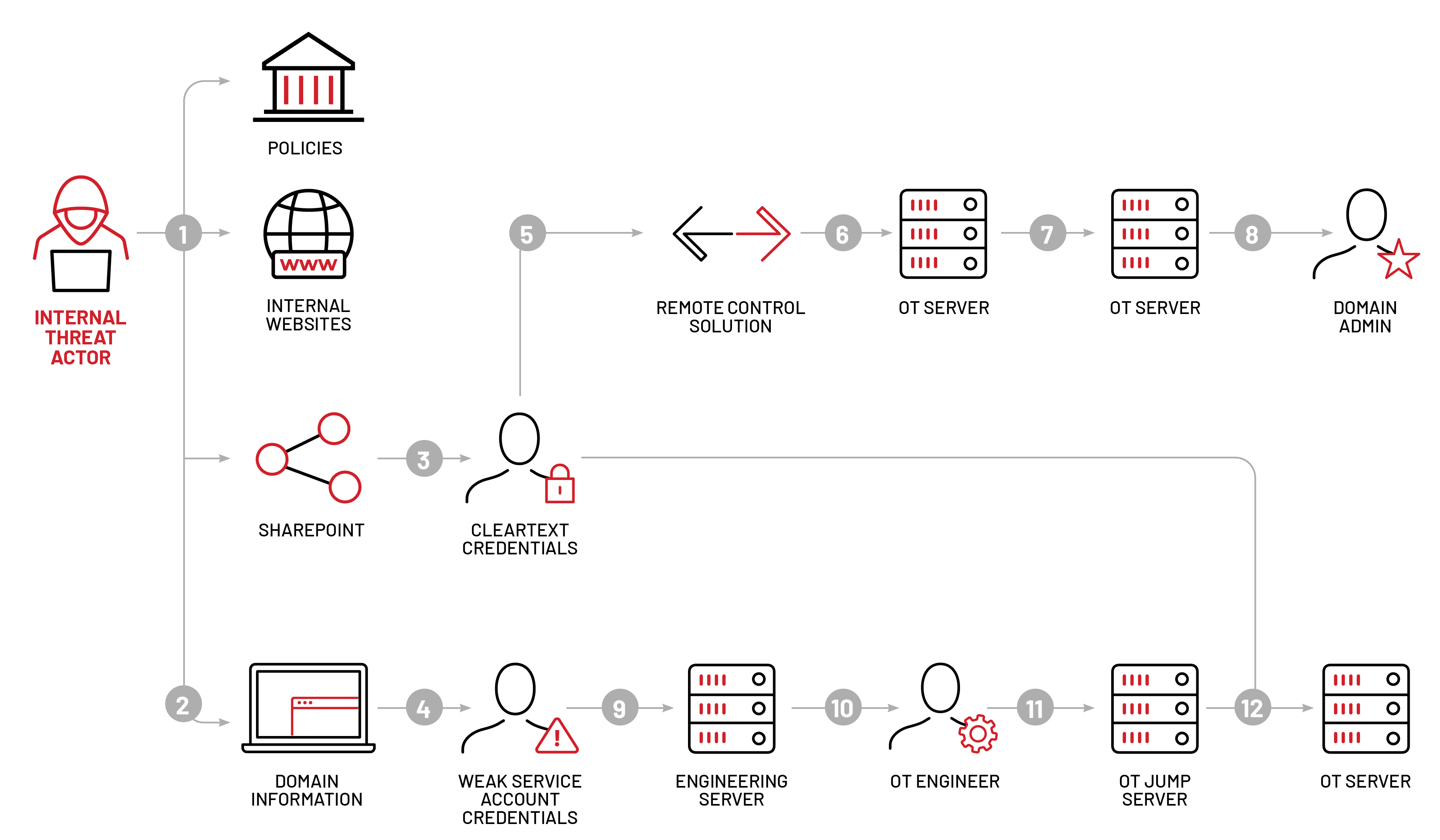
Mandiant Red Team Emulates FIN11 Tactics To Control Operational
OT Red Teaming Mandiant's Approach for OT Red Teaming Google Cloud Blog
OT Red Teaming Mandiant's Approach for OT Red Teaming Google Cloud Blog
Mandiants 'Creative' Red Team Review YouTube
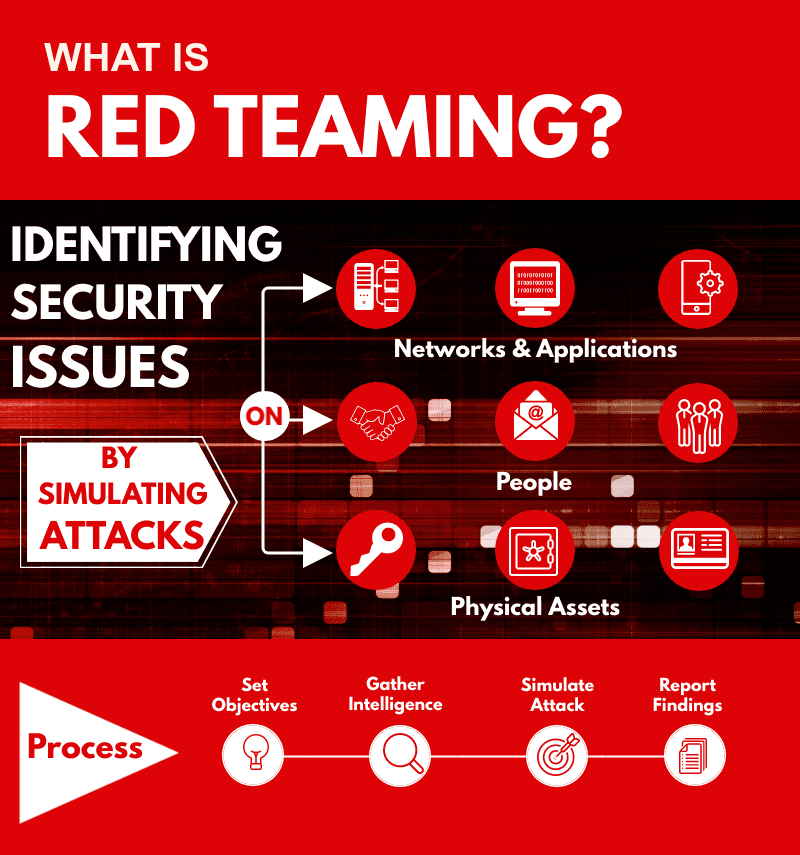
Red Teaming What It Is, Benefits, and How It Compares
Red Team Training Bundle
By Applying To This Position…See This And Similar Jobs On Linkedin.
This Course Draws On That Knowledge To Help Learners Improve Their Ability To Prevent, Detect, And Respond To.
See This And Similar Jobs On Glassdoor
This Course Includes Apis And Techniques Used To Perform Common Malicious Functionality And Extends These Techniques To Produce Reliable Payloads That Function Across Operating System.
Related Post: